Know Your Customer better – thanks to blockchain
Know Your Customer (KYC) is a process that covers a number of activities related to verifying the client’s identity and determining the potential risks of starting a business relationship with them. At GFT, we have developed a Hyperledger-based tool that addresses the client onboarding part of the KYC process. How does it work? Here we look at the business flow and our implementation of distributed ledger technology (DLT).
Throughout many projects, we observed how GFT’s clients continue to struggle every day with the difficulties of onboarding clients and managing the associated checks. We realised that much could be done to improve the processes and to consolidate the customer data, so we decided to build a modular proof-of-concept (PoC) application that implements the basic flow of the initial component of KYC – client onboarding. It contains a set of core functionalities that can be extended by adding new modules to support other aspects of the process.
Hyperledger Fabric
In order to address the issues related to KYC, we decided to use Hyperledger Fabric. This is a permissioned blockchain infrastructure which uses peer nodes with precisely defined roles to execute Smart Contracts (‘chaincodes’), then store the results in cryptographically safe and consistent blockchain structures.
What makes Hyperledger so well suited for a KYC solution? Most importantly, since Hyperledger Fabric uses blockchain structures, it offers an ‘append-only’, cryptographically consistent system of record (SoR). By design, it supports keeping “one version of truth” for sensitive client data. When an employee reaches for a piece of data, they automatically obtain the correct version, checked automatically by the logic of the interconnected nodes. They don’t need to reach out to any other employees, since the code itself takes care of consistency. What’s more, the information stored is immutable and cannot be changed. Again, it is the unique architecture that prevents tampering with the data. As a result, users of the application can trace the history of data changes and be certain that the registered changes are authentic and not forged.
Business flow
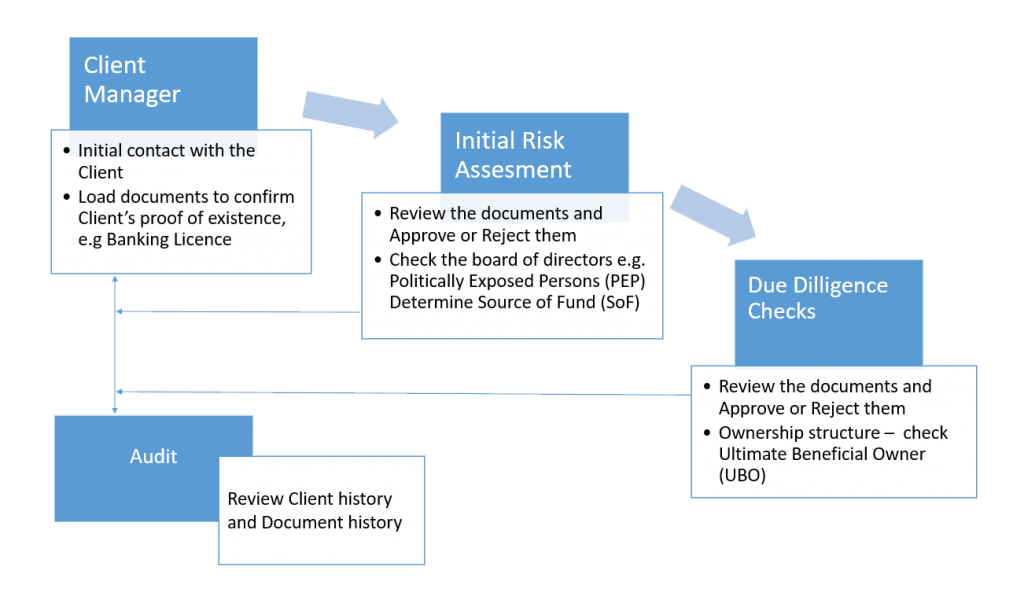
Taking this a step further, it is easy to see that data stored in this way can be securely re-used across the organisation. When the same client comes to buy a new product, the due diligence documents that were verified before can be used again, without repeating the lengthy and painful checks. A shorter and cheaper process means a happier client.
Safe re-using of data requires one more condition to be met – the precise definition of access to be granted only for specifically defined users. This is done by a deep permissioning system implemented via Smart Contracts. Data is guarded by cryptographic mechanisms, hence the user can access it only when permissions are assigned.
Here is a simplified business flow. Each step contains a list of documents, or data fetched from internal sources and publicly available databases. Each piece of information needs to be verified and confirmed, or rejected by an appropriate employee or responsible officer inside the organisation.
How to build a blockchain-powered KYC solution
Waldemar Trawnicki, Lead Developer at GFT, provides us with technical insight into the blockchain tool.

Lead Developer
Let’s take a look at how the actual blockchain tool is built. The first step is to create a consortium or structure that defines the set of departments in a network that are willing to conduct transactions with one another. In our case these are the ClientCenter, DueDiligence and RiskAssessment departments. Each of the departments has its own peer node which hosts:
- The ledger
- The CouchDB service that contains the world state
- The Membership Service Provider service
The second step is the creation of a ‘channel’. A channel is the primary communication mechanism by which the members of a consortium can communicate with one another. Channels are useful because they provide a mechanism for private communication and private data sharing between members of a consortium. They also provide privacy from other channels, and from the network.
Hyperledger Fabric is very powerful in this regard, as it allows departments to share infrastructure yet keep it private at the same time. There’s no contradiction here – different consortia within the network need different information and processes to be appropriately shared, and channels provide an efficient mechanism to do this.
Additional data privacy using customised private data collections
A private data collection is a combination of two elements. The first is the actual private data kept on a blockchain and sent peer-to-peer via the ‘gossip protocol’ to exactly the department that is authorised to see it. In our case, the department is able to see detailed information about the company and its representatives after sending a request, which then must be approved by the manager who owns the actual data.
The second element is a ‘hash’ of this data that is endorsed, ordered, and written to the ledgers of every peer on the channel. The hash serves as evidence of the transaction and is used for safe validation and can be used for audit purposes.
The components of the Hyperledger Fabric network mentioned can be perceived as different actors. Each of these actors (active elements inside or outside the network that are able to consume services) have a digital identity encapsulated in an X.509 digital certificate. These identities matter because they determine the exact permission over resources and access information that actors have in a blockchain network. Furthermore, a digital identity has some additional attributes that Hyperledger Fabric uses to determine permissions, and it gives the union of the identity and the associated attributes a special name – ‘principal’.
Principals are similar to UserIDs, but are more flexible, since they can include a wide range of properties of an actor’s identity, such as the actor’s organisation unit, role, or even the actor’s specific identity. For an identity to be verifiable, it must come from a trusted authority. This is achieved in Hyperledger Fabric thanks to a membership service. In our solution, each department has a separate MSP service that defines the rules that govern the valid identities.
In conclusion…
In order to achieve a business goal, you need to be equipped with the appropriate tools. As the complexity of business requirements continues to grow, old methods eventually expire, and this is when we should consider devising efficient new tools. For KYC processes, the integration of well-known mechanisms merged with new technologies, such as DLT and Smart Contracts, provides solutions that deliver new quality and a fresh approach to old issues. Our new tool is a great demonstration of this practical thinking in action to prove the use case for blockchain.
The team:




